karspersky Helpme
常规分析
查看内存快照的属性
|
|
查看内存快照的进程
|
|
dump 屏幕
|
|
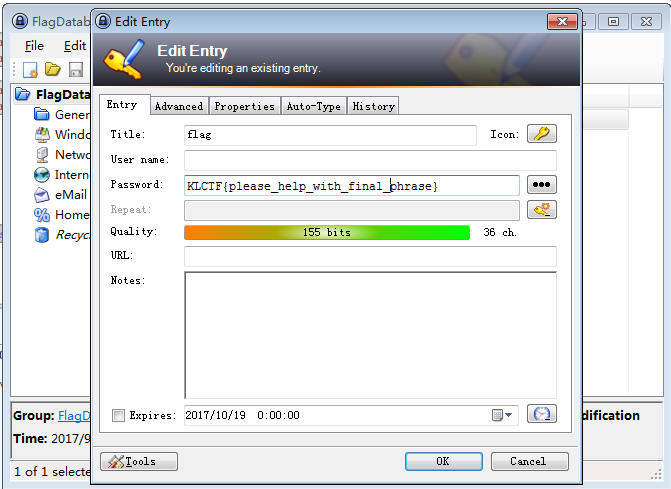
- 发现这个地方有问题,是用的KeePass秘钥管理软件开启了一个叫FlagDatabase.kdbx的数据库
- 于是,扫描文件
|
|
- Dump 下来再说
|
|
进一步分析
查找KeePass配置文件
|
|
Dump \Device\HarddiskVolume1\Users\user\AppData\Roaming\KeePass\KeePass.config.xml
|
|
分析配置文件
|
|
- 这里的UserAccount置位true,表明使用了windows 用户的 master key 进行加密
- 由于没有其他的加密选项,所以就是只用了windows的账户验证这一种加密
奔向答案
参考 http://www.harmj0y.net/blog/redteaming/a-case-study-in-attacking-keepass/
要恢复一个操作系统上用KeePass的windows账户验证加密的数据库,我们需要以下条件:
%APPDATA%\Microsoft\Protect\ 目录下的所有文件- Preferred
- master key file with a GUID naming (Windows账户主密钥文件)
- KeePass加密使用的软件主密钥
- ProtectedUserKey.bin
- Windows账户的信息
- UserDomain
- 密码
- SID
- UserName
- xxxx.kdbx 加密后的秘钥数据库
目前,我们缺少的就是:
- %APPDATA%\Microsoft\Protect\
目录下的所有文件 - KeePass加密使用的软件主密钥
- Windows账户的信息
搞SID目录下的文件
|
|
|
|
无奈之下,只好通过主密钥文件的特征进行搜索
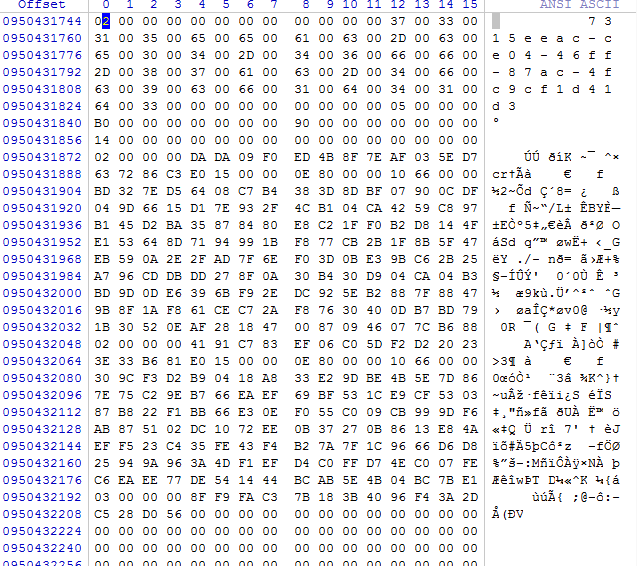
搞ProtectedUserKey.bin
|
|
搞用户信息
尝试hashdump,发现密码太长,搞不定
|
|
尝试rekall mimikatz,搞定
|
|
lsadump 也可以
|
|
密码是 yo_need_another_key_to_pass_this_level,真tmd长
搞账户信息
|
|
恢复KeePass加密数据
|
|
Restore-UserDPAPI脚本如下
|
|
会要求输入需要恢复的用户的密码,输入即可you_need_another_key_to_pass_this_level
打开KeePass,选择使用windows账户进行验证